About Me
Hello, my name is Yuanyi Sun (Screen name is HKHK) who is the owner of this site.
Currently I am a software engineer and prior to that, I received my PhD in Computer Science from Penn State University.
I am focused on backend development, security and privacy, computer vision, machine learning, and deep learning. I like coding. Most of my past projects written by Golang, Python, Pust, Javascript, C/C++, and Java.
Research:
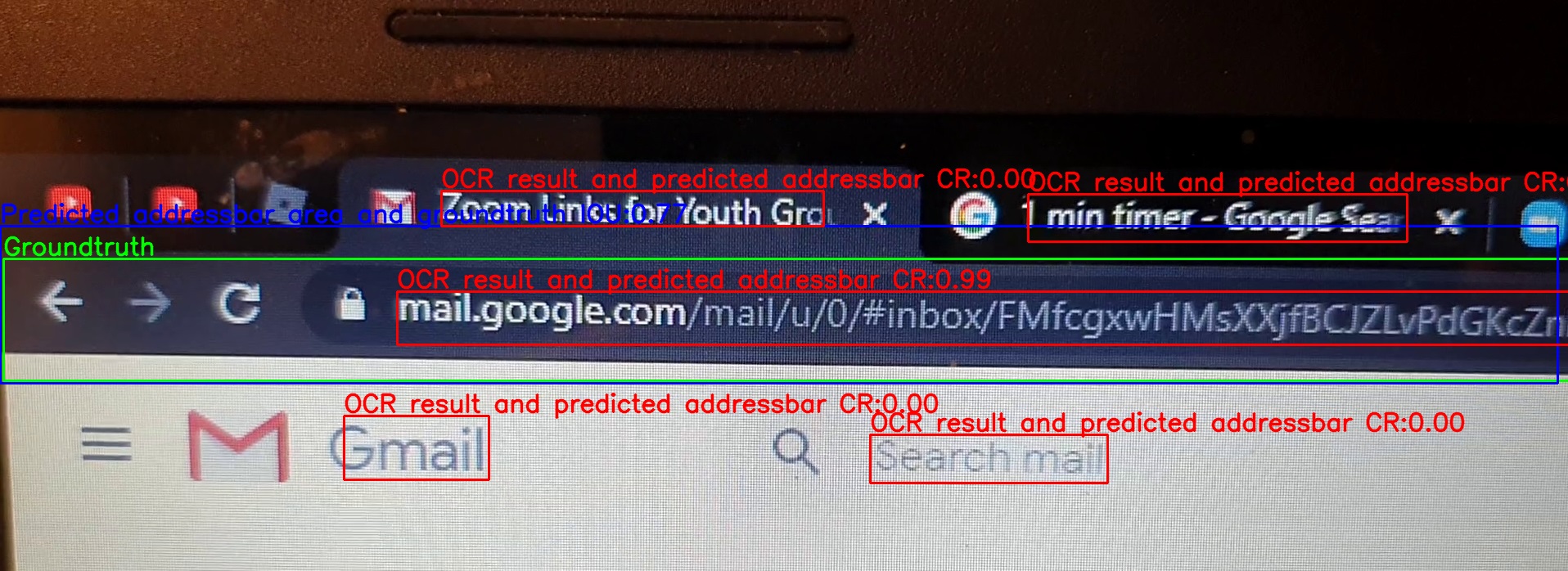
Y. Sun, S. Zhu and Y. Chen. ZoomP^3: Privacy-Preserving Publishing of Online Video
Conference Recordings. Proceedings of the 22nd Privacy Enhancing Technologies Symposium
(PoPETS), 2022. [paper]
Y. Sun, S. Chen, S. Zhu and Y. Chen. iRyP: A Purely Edge-based Visual Privacy-Respecting
System for Mobile Cameras.
Proceedings of the 12th ACM Conference on Security and Privacy in Wireless and Mobile Networks
(WiSec), 2020. [paper] [slides]
Y. Sun, S. Zhu, Y. Zhao, and P. Sun. A User-Friendly Two-Factor Authentication Method
against Real-Time Phishing Attacks. IEEE Conference on Communications and Network Security (CNS
2022). [paper]
Z. Xie, Y. Sun and S. Zhu AutoP3: A Privacy-by-Design Automatic Photo Privacy Protection
System for Mobile Cameras (Under review)
T. Xia, Y. Sun, S. Zhu, Z. Rasheed and K. Hassan-Shafique. Toward A Network-Assisted
Approach for Effective Ransomware Detection. EAI Transactions on Security and Safety, 2021. [paper]
P. Nagasubramaniam, C. Wu, Y. Sun, N. Karamchandani, S. Zhu and Y. He. Privacy-Preserving
Live Video Analytics for Drones via Edge Computing. Applied Sciences, Special Issue on Advances
and Application of Intelligent Video Surveillance Systems: Volume II, 14(22):10254, 2024. [paper]
Patent:
Photo Authentication Techniques Resistant to Real-time Phishing (Filed 2020)
Paper Reviewer:
SciSec 2018, ICICS 2018, ESORICS 2019, CNS 2020, ESORICS 2020, EAI
Endorsed Transactions on Security and Safety 2020, EAI Endorsed Transactions on Security and
Safety 2021, AsiaCCS 2022, IEEE Transactions on Mobile Computing, Cluster Computing, The Journal
of Supercomputing
Work experience:
Software Engineer (Meta, Feb 2025 - Present)
Software Engineer (Bytedance, Jan 2023 - Feb 2025)
Software Engineer (Zoom, Aug 2021 - Dec 2022)
Research/Teaching Assistant (Penn state university, June 2016 - Aug 2021)
Research Internship (Shape security, May 2019 - August 2019)
Research/Teaching Assistant (Stevens Institute of Technology, January 2015 - December 2015)
Skills:
Languages: Golang, Python, Rust, Javascript (Vue), C/C++, Java
Database: MySQL, MS SQL Server, PostgreSQL, MongoDB, NoSQL
Networks: Nginx, IIS, Apache, XML, Html, Load-Balance, Socks proxy, Reverse proxy, VPN, CDN,
Intelligent DNS, Network attack analysis
Others: Reverse engineering/Cracking, Unity3D, UDK, MFC, WPF, Win 32 API, COM, Socket
programming, Multithread programming, GDI/Html layout User Interface
Selected Software/Tools:
HK2.IO Cloud Disk: A URL shorten, file sharing, online preview, and cloud download
services provider.
The system is based on the asynchronous technique. Frontend: JS+Vue+element. Backend:
FastAPI+Go. To improve efficiency, backend python is compiled to binary code. To support big
file uploading, the frontend divides a big file into chunks. Nginx uses revere proxy to assign
works to different applications.
Demo
x86 Memory Codes Injection and SSDT API Inline Hook
Written in C++ and assembly. Memory codes injection is for the case when we need to inject our
codes to another process for running. First, open the target process. Virtual allocate
appropriate space for codes to be running. Write process memory into space and create a remote
thread to run it. Source code: hk2.io/d
SSDT inline hook is usually for Ring0 level security. Get the original address from Service
Descriptor Table. Calculate target function (e.g., NtOpenProcess) offset. Save the original
function address and jump to the handler function by the unconditional branch instruction. When
finishing, jump back to the original address.
Lightweight high-efficiency memory NoSQL database.
The goal of this project is to build a high-efficiency NoSQL database. The core hash function is
written by assembly language to achieve high efficiency. The hash function can be inlined into
other projects.
Lightweight intelligent DNS server:
Currently, the widely used DNS service only returns random IP from load balance. It does not
consider location, connection information between users and servers. In this project, the goal
is making the DNS service more intelligent. When a user queries our DNS, considering connection
and location, the intelligent DNS will return the best IP between the user and server to achieve
better performance. Another improvment is using dynamic TTL, based on delay, delay jitter,
speed, etc.
English input method: Intelligent complete words and adjust the position of a comma.
This project is improving English inputting efficiency in a computer. The system can
auto-complete the word you input and auto adjust the position of a comma or number in a
sentence. This project relates to multithread programming and database querying.
Demo
Hobby: The following videos are clips of me playing Transcendental Etude Mazeppa (S.139
No.4) and Grandes Etudes de Paganini La Campanella (S.141 No.3) by Franz Liszt.
Backend Development
Security and Privacy
Computer Vision
Machine/Deep Learning
Penn State University
Computer Science
Ph.D.
Software Engineer
Researcher
Research/Teaching Assistant
Services
Security and Privacy
System security and privacy analysis. Build a robust system.
Computer vision
Working with computer vision library like OpenCV, PIL.
Machine/Deep Learning
Working with object detection like Yolo, Mask RCNN, DeepLab, etc.
Software
Here is the gallery of my past software.
- All
- App Development
- Computer Vision
- Machine/Deep Learning
Contact
Contact us.